You are here:
WindowsShareware.com > Featured Products > ActiveXperts Network Monitor > Windows > Anti-Virus Check > SophosMonitor Sophos Anti-Virus status on your network computers
Monitor Anti-Virus and Internet Security suites
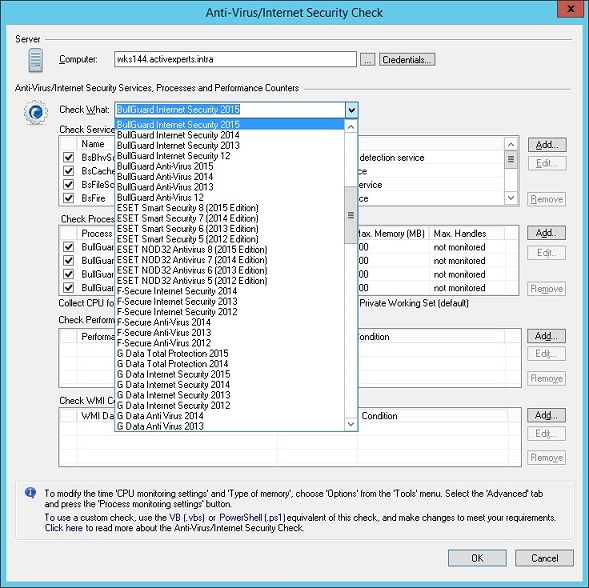
With ActiveXperts Network Monitor, you can monitor most important Anti-Virus and Internet Security suites available today. Simply select 'New Monitoring Check' from the 'Monitor' menu, select the 'Anti-Virus / Internet Security' check and fill in the required parameters.It checks the Sophos Anti-Virus services and processes, and optionally checks the virus definition files to see if version and/or date of the files are OK. The check can easily be extended by the user to monitor additional aspects, e.g. log files, dll versions of the software, number of files in quarantine, etc.
Monitor Sophos Anti-Virus
You can configure the Sophos Anti-Virus check in the ActiveXperts Network Monitor dialog below, to see if the software is running properly.
About Sophos Anti-Virus
Sophos Anti-Virus analyses behavior of the programs running on the system. The runtime behavior analysis includes:
- Suspicious behavior detection - dynamically analyzes the behavior of all programs running on the system, in order to detect and block activity which appears to be malicious. Suspicious behavior may include changes to the registry that could allow a virus to run automatically when the computer is restarted.
- Buffer overflow detection, which dynamically analyzes the behavior of all programs running on the system, in order to detect buffer overflow attacks.
- Suspicious file detection - Sophos Anti-Virus can scan for suspicious files, that is, files that contain certain characteristics that are common to malware but not sufficient for the files to be identified as a new piece of malware. For example, a file containing dynamic decompression code commonly used by malware can be regarded as suspicious.
- Application control - From Enterprise Console, you can configure Sophos Anti-Virus to detect and block 'controlled applications', i.e. legitimate applications that are not a security threat, but that you decide are unsuitable for use in your office environment. Such applications may include games, instant messaging (IM) clients, Voice over Internet Protocol (VoIP) clients, digital imaging software, media players, or browser plug-ins.
